One of the major headlines in recent news is Edward Snowden’s revelation of documents which prove that the US government is using high-tech software to gather massive amounts of private information on every-day Americans.
Snowden has taken bold action against the government in an effort to publicize the government’s violation of constitutional rights and to “inform the public as to which is done in their name and that which is done against them”.
Snowden has offered himself as the main proponent in this political debate by revealing himself as the source of covert documents which blatantly violate privacy rights. In doing so he has subsequently linked himself to a debate which will likely have personal ties for years to come. Snowden recognizes the dangers he is incurring but believes he has a greater duty to impede the government from destroying “privacy, internet freedom, and basic liberties for people around the world”.
As one would presume, much speculation – from both sides of the debate – has followed this heavily disputed announcement. Snowden has asserted that the government is unlawfully collecting phone records and surveilling internet activities. Government officials have vigilantly denied these accusations. House Intelligence Committee Chairman Mike Rogers spoke on the issue saying “He doesn’t have a clue how this thing works; neither did the person who released just enough information to literally be dangerous… I absolutely think [the leaker] should be prosecuted.”
The press has also taken part in the debate narrating the ongoing story, generally backing Snowden. After Snowden’s release, the Guardian and Washington Post have released various articles on the matter most of which distort the extent to which the Government has manipulated private information.
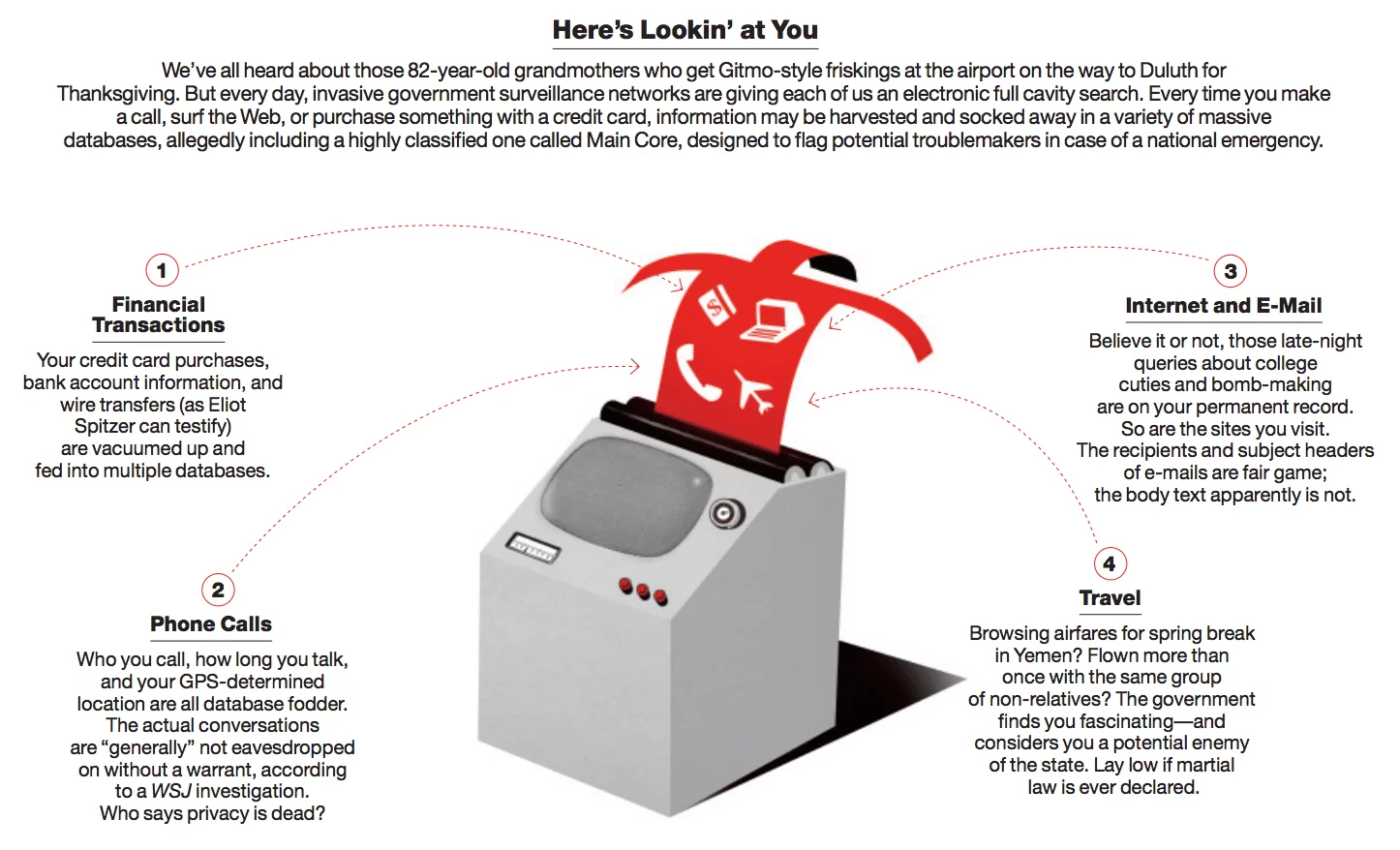
Amidst all of the publicity surrounding the leaks, journalist Christopher Ketcham (who previously won acclaim by covering the tragic events on 9/11) released a relevant new article discussing the secretive exploits of a governmental unit which gathers boundless amounts of information on Americans. Ketcham details programs by the government designed to fight crime by predicting criminal behavior before it is committed and to predict behavioral responses to propaganda and government-inflicted terror.
Both programs rely on keeping tabs on citizens and gathering data by tracking phone calls, credit card receipts, social networks, GPS tracks, Internet searches, Amazon purchases and E-Z pass records.
The program based out of Purdue University’s Synthetic Environment for Analysis and Simulation Laboratory is titled Sentient World Simulation (SWS). This 9-page PDF released by Purdue itself describes the project in adequate detail.
The simulator has taken the spying that Snowden publicized, one step further. The program has amassed databases so profound they can now look so deep into a person’s life they can predict their thoughts and future actions with relative certainty. Although this system is incredibly intrusive and raises many moral concerns, it provides valuable insight into questions which could be extremely beneficial. It’s unclear as to weather all the private-sector efforts towards transparency (including some noteworthy AI projects at Microsoft) will have any effect on the direction and intensity of public-sector surveillance.
By gathering enough intelligence SWS is capable of producing realistic simulations of various different scenarios such as natural disasters, foreign and domestic attacks, resource shortages, and hazardous economic trends. The program, once finished will utilize the information from its colossal database to create these hypothetical situations, predict possible outcomes, and test the effectiveness of various responses. Researchers hope the system will be able to provide effective answers to complex questions which baffle the most skilled thinkers and will create more efficient methods of responding to catastrophes.
Even with the tremendous advantages SWS will offer, we must be wary that the NSA – a government program which is top-secret and has access to an abundance of private information – does not abuse its authority and violate privacy acts with extracurricular motives. The program must be scrupulously overlooked so that it does lead other government programs and companies to believe that it is acceptable to disregard moral and ethical code in replacement for efficiency.
In the midst of a technological wave, the inherent ability of humans to use “gut-feelings” to make conscious decisions probably shouldn’t be forgotten entirely. Technology and data can be valuable resources in calculating the risks and rewards of important decisions but no technology can replace human instinct. While we’ve previously conducted research on the risks of artificial intelligence, the future may require a more robust assessment of how AI is used in the great trade-off of safety and privacy.
The original research for this article was completed by Colin Patch.