Biometric solutions are typically used for security and access control across businesses and government organizations. The U.S. government has taken keen interest in biometric applications and has been aggressively funding advanced research programs in businesses that offer biometrics.
The Intelligence Advanced Research Projects Activity (IARPA), a U.S. government organization that funds academy and industry research, announced the launch of the Odin program in October 2017. Odin aims to develop biometric presentation attack detection technologies to better identify unauthorized user attempts and imposters. IARPA’s other programs such as Biometrics Exploitation Science & Technology and Janus also aim to “significantly advance biometric technologies.”
In April 2017, IARPA awarded AI biometric solutions provider Crossmatch a contract of $5.8 million to “develop next-gen biometric presentation attack detection technologies.” In June 2017, it funded a four-year $12.5 million contract to SRI International, an independent, nonprofit research center to “address vulnerabilities in the current biometric security systems,” specifically, fingerprint, iris and face scanners.
Biometric technology has captured the interest of many investors outside of IARPA as well. SenseTime, a Chinese AI company that offers a range of AI business solutions, including biometrics says it set a record by raising $410 million in July 2017.
How AI Biometric Technologies Work
There are two categories of biometric identification and recognition solutions: Physical and behavioral.
Physical biometric solutions use distinctive and measurable characteristics of particular parts of the human body, such as a person’s face, iris, DNA, vein, fingerprints, etc., and transform this information into a code understandable by the AI system.
Behavioral biometric solutions operate in a similar way, except they use unique behavioral characteristics, such as a person’s typing rhythm, way of interaction with devices, gait, voice, etc. This encoded biometric information is stored in a database and digitally sampled during authentication and verification.
Face Recognition
A facial recognition biometric system identifies and verifies a person by extracting and comparing selected facial features from a digital image or a video frame to a face database. For example, an algorithm may analyze the distance between the eyes, the width of the nose, the depth of the eye sockets, the shape of the cheekbones, the length of the jaw line, etc., and encode the corresponding data as “face prints,” which can then be used to find appropriate matches in a destination database.
Readers with a deeper interest in facial recognition may want to explore our full article about facial recognition applications.
Speaker (Voice) Recognition
Speaker or voice recognition differs from speech recognition in that the former recognizes and identifies a speaker using voice biometrics and the latter analyzes what is being said. Voice biometrics include both physical characteristics, such as the shape of the vocal tract responsible for articulating and controlling speech production, and behavioral characteristics such as pitch, cadence and tone, etc.
Voice biometric solutions digitize words by reducing them to segments comprising encoded frequencies or formants and produce a model “voice print” unique to a person. This voice print is used for identification and authentication of the speaker. Our previous coverage on natural language processing has explored voice recognition in greater depth.
Fingerprint Recognition
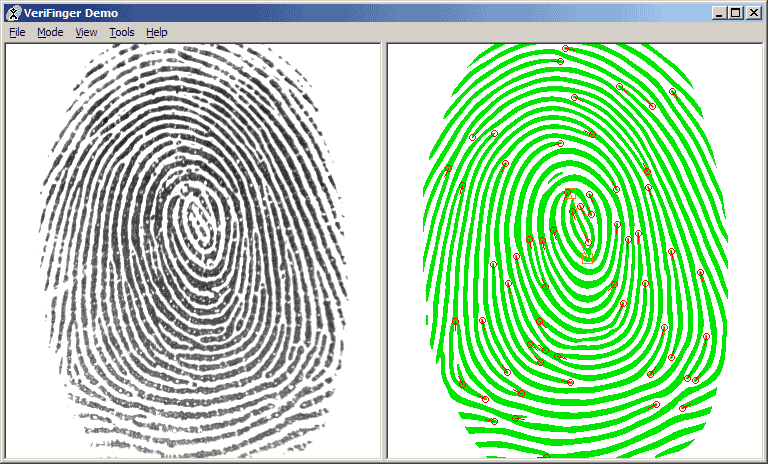
Most fingerprint biometric solutions look for specific features of a fingerprint, such as the ridge line patterns on the finger, the valleys between the ridges, etc., commonly known as minutiae, which are then converted to stored digital data. In order to get a fingerprint match for verification or authorization, biometric systems must find a sufficient number of minutiae patterns. This number varies across systems.
Behavioral Biometrics
Behavioral biometrics identify and measure human activities, such as keystroke dynamics, voice print, device usage, signature analysis, error patterns (accidentally hitting an “l” instead of a “k” on two out of every fifth transaction), etc. Such behavioral biometrics are typically used as an additional layer of security, along with other credential or biometric information.
Most physical biometric solutions systems authenticate the user only once and usually at the beginning of an action, such as logging into a device or opening a door. Behavioral biometric technology attempts to fill the gap of authentication in a scenario during an action.
For instance, the original user may provide his/her credentials to another person after the user has been successfully authenticated (akin to tailgating). In order to minimize such possibilities in this case, behavioral biometric solutions analyze users’ interactions with their devices, recording activities that vary from normal usage patterns.
Organizations Offering Biometric Solutions
Crossmatch – ‘Composite’ Biometric Authentication
Crossmatch claims to be a “risk-based composite authentication and biometric identity management” company. In 2014, it merged with Digital Persona, another biometric company, to launch its key biometric solution platform for enterprises called DigitalPersona Composite Authentication.
The platform offers the “broadest set of authentication factors,” including fingerprint scanning, face and voice recognition, and behavioral biometrics, such as keystroke, swipe and mouse action tracking, the company said. In November 2017, Crossmatch announced its partnership with BehavioSec , a Sweden-based behavioral biometrics company, which powers the behavioral biometric analyses functions of DigitalPersona.
In September 2017, Crossmatch partnered with Oxford Computer Group, a Microsoft Gold Partner that offers identity and security solutions. This announcement claims that the DigitalPersona software will be offered to Oxford’s Microsoft customer base.
Apart from the enterprise platform, the company also seems to offer a wide range of biometric solutions, most notably, fingerprint scanning and detecting solutions across various business sectors, including finance, government, law enforcement, retail, etc.
The video below shows use cases of its various biometric solutions for law enforcement, including the Digital Persona Mobile ID, an app that comes with fingerprint recognition software, which helps store and identify security and agency personnel through their biometric information.
Tygart Technology – Facial Recognition from Videos
Tygart Technology said it provides video and photographic analysis as well as biometric recognition systems for state and federal government clients in the United States.
Its key product is MXSERVER, a server-based “video and photo forensic analysis system.” The system processes video and photo collections extracted from confiscated computers, mobile phones, SIM cards and video surveillance systems into searchable resources. The company also said it serves the FBI by providing operation and maintenance services for its automated, national fingerprint identification system.
The video below re-enacts a “real-word scenario,” where MXSERVER could be put to use.
MXSERVER “will help prevent criminal and terrorist attacks from being carried out.” Facewatch is a London-based firm that uses the MXSERVER facial recognition platform to help businesses and police “tackle low-level crime.” The system supposedly alerts businesses when registered criminals enter the premises. It does so by matching the facial biometric information stored in a centralized watchlist.
Recently, Facewatch announced its facial recognition system installed in BRMalls in Brazil helped “capture five serious criminals in the first two months of use.” That story – and a number of other Facewatch testimonials – were covered in depth by American Security Today in October 2017. Facewatch is currently using MXSERVER as its facial recognition engine, although it can work with any system.
Readers with a particular interest in AI for crime detection should read our previous article titled AI for Crime Prevention and Detection – 5 Current Applications.
Onfido – Facial Biometrics
London-based Onfido is an online digital verification platform for businesses. Among other compliances and clearances, Onfido also uses facial biometrics, as an additional layer of security, to verify individual persons. The company said it uses machine learning technology to validate a user’s identity and cross-reference it against international credit and watchlist databases.
The video below demonstrates the use of facial biometrics on the Onfido mobile website, which seems to be integrated with a banking platform. The volunteer is asked to verify her identity using two steps. First, photos of her driver’s license are scanned online.
Then, she is informed that she has to be authenticated via a “selfie” video. This, the application explains, is to make sure she is not being impersonated. In the “selfie” video, she is instructed to perform two simple steps such as turning her face to the left/right and saying the indicated numbers out loud. It is not clear from the demo or the website whether voice recognition is also part of the verification process.
The company has raised more than $60 million from big firms such as Microsoft Ventures, Salesforce Ventures and Crunchfund. More recently, Crane Venture Partners invested $30 million to fund the company’s R&D in machine learning technology.
The company customers include ZipCar, Couchsurfing, Revolut and Square. Very recently, it launched its onboarding platform on the Salesforce AppExchange.
EyeLock – Iris Recognition
EyeLock said it offers “advanced iris authentication for the Internet of Things.” Its signature product, Nano NXT, is a iris biometric recognition hardware. Nano NXT has a false acceptance rate (the likelihood of the biometric security system accepting an unauthorized user) of 1 in 1.5m in a single eye.
The video below demonstrates a proof-of-concept ATM from EyeLock and Diebold-Nixdorf, a provider of connected retail services, including smart ATMs and kiosks. This “ATM of the Future” appears to require no card or PIN number. The ATM is integrated with the EyeLock iris biometric technology, which combined with the phone banking app, recognizes the user and gives them access to withdraw cash.
The company says it owns more than 75 patents for its proprietary biometric technology. It also cites various partners that use and resell its biometric solutions. Its most recent partnerships include STANLEY Security Solutions, ViaTouch Media and Central Security Distribution.
Fujitsu Frontech – Vein Recognition
Japan-based Fujitsu Frontech’s signature biometric solution is the PalmSecure Sensor, an authentication device that scans the veins in the palm without the user having to make contact with the device.
A 2015 animated video explains this technology and how the biometric information is stored in the database.
In May 2017, the company announced that Fujitsu Korea and Fujitsu Frontech partnered to provide the vein recognition solution to Korea’s Lotte Card Co Ltd to facilitate a cardless and cashless payment system. “PalmSecure does not save palm vein info in the shape of an image but rather it changes the vein pattern info into data that cannot be deciphered, and then encrypts that data,” the company said.
Reduced hemoglobin inside the vein absorbs near infrared rays that makes it possible to “distinguish vein patterns that differ from person to person,” the firm added. Also, since the vein patterns do not change, as do other biometric factors, this process involves only a one-time registration.
As of March 31, 2017, about 770,000 PalmSecure devices have been shipped to 60 countries, and more than 70 million people make use of this biometrics device, Fujitsu said.
BehavioSec – Behavioral Biometrics
Sweden-based BehavioSec said it uses continuous machine learning to authenticate users based on their behavior patterns, such as pressure, gyroscope, button hit zone, motion, accelerometer, mouse actions, etc.
BehavioSec’s demo video explains how this technology works:
In 2012, the U.S. Defense Advanced Research Projects Agency invested in its technology, the company said. However, it does not mention for how long the funding was in process or how much money was involved. BehavioSec also said it secures more than 5 billion transactions a year, although it did not provide information on the types of transactions.
Recently, the BehavioSec technology has been integrated into Crossmatch’s DigitalPersona platform.
Future Revenue Forecasts in Biometrics
According to a 2017 Tractica report, biometrics hardware and software revenue will grow to $15.1 billion worldwide by 2025, with a CAGR of 22.9 percent. The report also predicts that the cumulative biometrics revenue from 2016 to 2025 will total $69.8 billion.
The report analyzes 142 use cases and infers that the largest revenue segments of biometrics will be fingerprint recognition, voice recognition, iris recognition and facial recognition. The largest application markets for the biometric technologies, according to the report, will be consumer, finance, healthcare, government and enterprise-level physical and IT security.
The iris recognition market will grow from $676.6 million in 2016 to $4.1 billion by 2025, according to the report. During this 10-year period, global shipments of iris recognition devices will increase from 10.7 million units to 61.6 million units annually, with 277.4 million cumulative shipments.
Global enterprise biometrics revenue will reach $1.7 billion by 2024, with a cumulative revenue of $7.9 billion from 2015-2024, at a 28% CAGR, according to a 2016 Tractica report. Healthcare and finance industries show the most potential for revenue growth within the 10-year period of 2015-2024, the report added.
Header image credit: ZKTeco Philippines